In Entra ID under Devices, All Devices and then Device Settings, you can enable: Require Multifactor Authentication to register or join devices with Microsoft Entra.
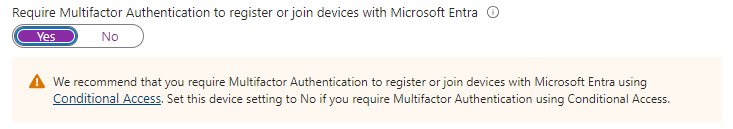
However Microsoft recommends disabling this feature (enabled by default) and enforcing via a conditional access policy instead.
This guide provides 2 ways of achieving that goal.
Method 1:
This method will require users for MFA in any cases, thereby this policy is not only for requirement of MFA upon first device registration, but requires MFA the second you set this policy to On.
- In Entra ID under Protection, Conditional Access and then Policies, choose new policy from template.

- Choose “Require multifactor authentication for all users

- Select Review and Create, and then Create. Notice that your signed-in user will be auto-excluded by this policy. (Make sure your user is enforced by MFA in another way or else remove your user from excluded users after creating policy. Always make sure you have a break-glass account configurered correctly before including your own user)

- Change the policy from report-only to On.
Method 2:
This policy is more granular and will only apply then users try to register devices for the first time. This policy is also a good example of how to create a custom policy to exclude certain users from this requirement (ect. kiosk devices at named location). However keep in mind that exclusions from one policy, does not mean that users will not be required for MFA at all if another policy hits the user. Therefore exclusions should be constructed together with other include policies.
- In Entra ID under Protection, Conditional Access and then Policies, choose new policy.

- Name the policy “Require Multifactor Authentication to register or join devices with Microsoft Entra”.
- Under Users, select All users. Exclude your self if you want to, but not required since we are only going to target a specific action in later step.

- Under Target resources, switch from default cloud apps to user actions, and then check “register or join devices”.

- Under Grant, check “Require multifactor authentication”.

- Set the policy to On and then hit Create.


Comments