Intro
This guide will assist in the proces of exporting inventory from Defender for Endpoint. This export will both export servers and clients that are registrered in Defender for Endpoint, since servers also registrer to the same inventory as clients.
It can be useful then you want to export data about high exposure devices, or get IP addresses of all devices. You can also validate if any device is not fully onboarded.
The script will output in CSV format, to the path where PowerShell session is showing. The file will be called: DefenderEndpoint-ExportedInventory.csv

Prepare Entra ID App Registration
Create app registration
Go to Entra ID, and navigate to Applications, App registrations. Then create a new App registration.
Name: Defender for Cloud – Reports
Under Supported account types, Who can use this application or access this API, Choose:
Accounts in this organizational directory only (tenant name only – Single tenant)
Then hit Register.
Create secret
Now go to the newly created app registration. Under Certificate and Secrets, create a secret (set expire to 3 months), and then add it.

Now copy the value for the secret (OBS: this will only be possible doing creation, after you close the browser tab and re-visit the secrets page, part of the value will be hidden and secret retrival will not be possible. (Then you would have to create new secret))

Save the secret in a secure location (NOT in the script).
Set API permissions
Under API permissions, add application permissions of type WindowsDefenderATP and permissions Machine.Read.All.
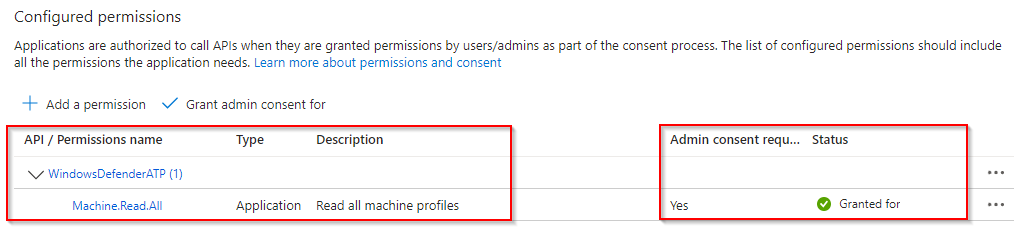
REMEMBER to grant admin consent after adding the permission.

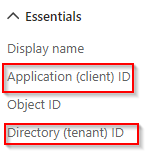
Get app info
Go to the overview page of the app registration, and take note of Application (Client) ID and Directory (Tenant) ID.
Script preparation
The first 2 lines of the script must be edited with info from the app registration.
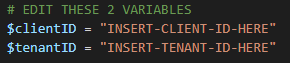
# EDIT THESE 2 VARIABLES
$clientID = "INSERT-CLIENT-ID-HERE"
$tenantID = "INSERT-TENANT-ID-HERE"
# DO NOT EDIT BELOW THIS LINE
$clientSecret = read-host "Input secret for app registration"
$resourceAppIdUri = 'https://api.securitycenter.microsoft.com'
$oAuthUri = "https://login.microsoftonline.com/$TenantID/oauth2/token"
$body = [Ordered] @{
resource = "$resourceAppIdUri"
client_id = "$clientID"
client_secret = "$clientSecret"
grant_type = 'client_credentials'
}
$response = Invoke-RestMethod -Method Post -Uri $oAuthUri -Body $body -ErrorAction Stop
$aadToken = $response.access_token
$Headers = @{
"Authorization" = "Bearer $($AccessToken)"
"Content-type" = "application/json"
}
$url = "https://api.security.microsoft.com/api/machines"
$headers = @{
'Content-Type' = 'application/json'
Accept = 'application/json'
Authorization = "Bearer $aadToken"
}
$webResponse = Invoke-WebRequest -Method Get -Uri $url -Headers $headers -ErrorAction Stop
$response = $webResponse | ConvertFrom-Json
$response.Value | Export-CSV -Path ".\DefenderEndpoint-ExportedInventory.csv" -Delimiter "," -NTI
Now save the whole script in a path of your choosing. Format must be .ps1 format.
Execute script
Open PowerShell 7 and execute the script.
Then asked, input the secret for the app registration
After script is finish, a CSV file will be visible in the folder PowerShell session was running in.


Comments