Before you begin
If you have hybrid joined session hosts, remember to first setup SSO using this guide:
Azure Virtual Desktop – Entra ID SSO – Complete Guide – Christoffer Klarskov Jakobsen – Microsoft Architect
Then configuring AVD, and we have spend some time setting up a nice SSO experience for the users, it is frustrating to see the consent prompt thenever users sign-in to new session hosts. This simple configration overcomes that issue.
Create Dynamic Group in Entra ID
You can use multiple expressions, but the simple configuration is to use the start of the name of the session hosts in our host pool, since we use DevOps pipelines to control deployment of session hosts and a controlled naming convention:
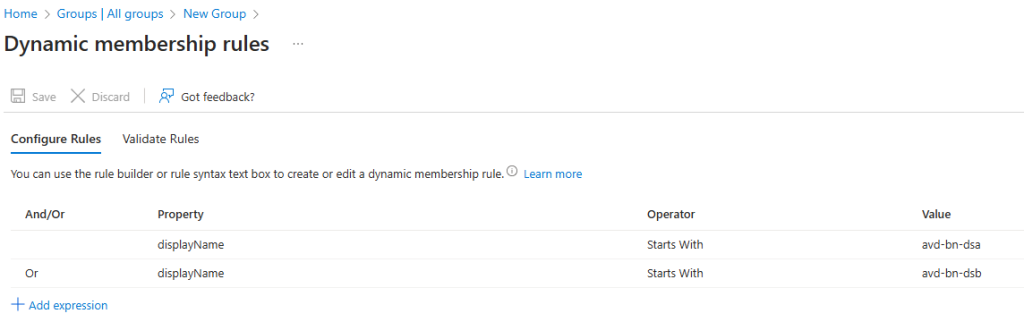
Give the group the name: SGD-AVD-SessionHosts
Configure permissions for Built-in App Registrations
Import-Module Microsoft.Graph.Authentication
Import-Module Microsoft.Graph.Applications
Connect-MgGraph -Scopes "Application.read.all", "Application-remotedesktopconfig.readwrite.all", "Directory.Read.All"
$MSRDSpId = (Get-MgServicePrincipal -Filter "AppId eq 'a4a365df-50f1-4397-bc59-1a1564b8bb9c'").Id
$WCLSpId = (Get-MgServicePrincipal -Filter "AppId eq '270efc09-cd0d-444b-a71f-39af4910ec45'").Id
If ((Get-MgServicePrincipalRemoteDesktopSecurityConfiguration -ServicePrincipalId $MSRDspId) -ne $true) {
Update-MgServicePrincipalRemoteDesktopSecurityConfiguration -ServicePrincipalId $MSRDspId -IsRemoteDesktopProtocolEnabled
}
If ((Get-MgServicePrincipalRemoteDesktopSecurityConfiguration -ServicePrincipalId $WCLspId) -ne $true) {
Update-MgServicePrincipalRemoteDesktopSecurityConfiguration -ServicePrincipalId $WCLspId -IsRemoteDesktopProtocolEnabled
}
Get-MgServicePrincipalRemoteDesktopSecurityConfiguration -ServicePrincipalId $MSRDspId
Get-MgServicePrincipalRemoteDesktopSecurityConfiguration -ServicePrincipalId $WCLspId
Link dynamic group with service principals
$GroupID = (Get-MgGroup -Filter "DisplayName eq 'SGD-AVD-SessionHosts'").Id
$tdg = New-Object -TypeName Microsoft.Graph.PowerShell.Models.MicrosoftGraphTargetDeviceGroup
$tdg.Id = $GroupID
$tdg.DisplayName = "SGD-AVD-SessionHosts"
New-MgServicePrincipalRemoteDesktopSecurityConfigurationTargetDeviceGroup -ServicePrincipalId $MSRDspId -BodyParameter $tdg
New-MgServicePrincipalRemoteDesktopSecurityConfigurationTargetDeviceGroup -ServicePrincipalId $WCLspId -BodyParameter $tdg
Hybrid Joined session hosts
Create a Kerberos server object
If your session hosts meet the following criteria, you must create a Kerberos server object.
- Your session host is Microsoft Entra hybrid joined. You must have a Kerberos server object to complete authentication to a domain controller.
- Your session host is Microsoft Entra joined and your environment contains Active Directory domain controllers. You must have a Kerberos server object for users to access on-premises resources, such as SMB shares and Windows-integrated authentication to websites.
You can follow this guide on how to setup Kerberos Server object: Windows Hello for Business Cloud Kerberos Trust – Christoffer Klarskov Jakobsen – Microsoft Architect
Important
If you enable single sign-on on Microsoft Entra hybrid joined session hosts without creating a Kerberos server object, one of the following things can happen when you try to connect to a remote session: * You receive an error message saying the specific session doesn’t exist. * Single sign-on will be skipped and you see a standard authentication dialog for the session host. To resolve these issues, create the Kerberos server object, then connect again.
Important
When single sign-on is enabled, a new Microsoft Entra ID app is introduced to authenticate users to the session host. If you have conditional access policies that apply when accessing Azure Virtual Desktop, review the recommendations on setting up [multifactor authentication](https://learn.microsoft.com/en-us/azure/virtual-desktop/set-up-mfa) to ensure users have the desired experience.

Comments