This article is part of a series: Microsoft Global Secure Access – Private Access – Christoffer Klarskov Jakobsen – Microsoft Architect
Table of Contents
Intro
I have created an Entra ID joined VM in Azure running Windows 11 Pro 24H2. The user I test with has been assigned Microsoft 365 E3 + Microsoft Entra Suite licenses (if you fail to assign license to your test user, you will face the status in the client: disabled by your organisation. However this error can also occur if no forwarding traffic policies have been assigned to the user)
Validate
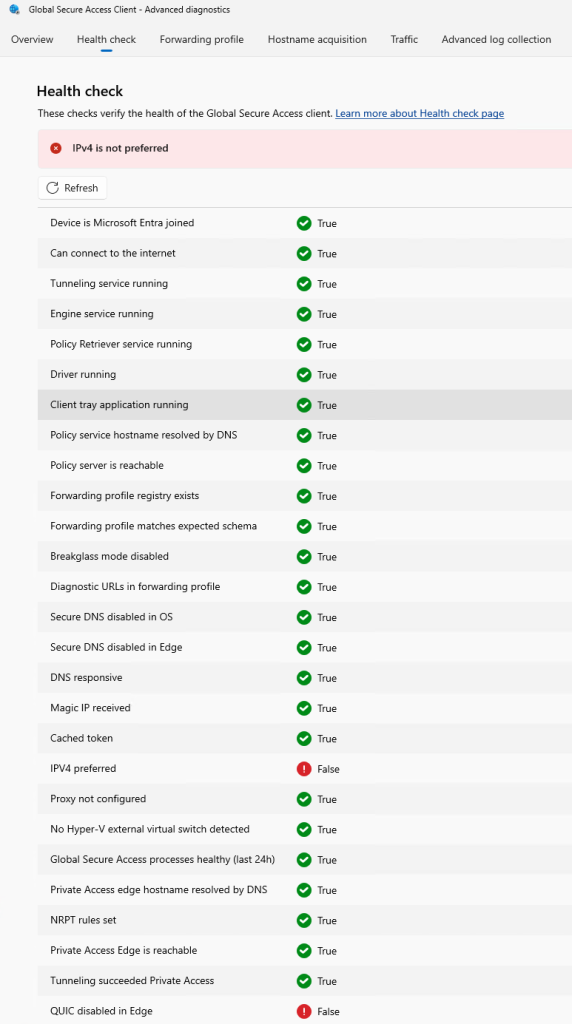
To validate the configration I open the Advanced Diagnostics within Global Secure access:

Under Health Chech, you can monitor the current state (note I have a few issues to troubleshoot, but overall the client works at this stage):
Under Forwarding profile, you can see the rules applied to the client:

If I use PowerShell to test connection to target application and port, I can see that the port 445 is open:

My client it not domain joined and I have not setup Cloud Kerberos Trust for this demo, so after beeing prompted for credentials for the domain, I was able to browse a share on the target application server:


Comments