Source: Microsoft Entra Password Protection – Microsoft Entra ID | Microsoft Learn
Huge credits to Ali Tajran: Configure Microsoft Entra Password Protection for on-premises – ALI TAJRAN
Requirements
License Requirements
| Scope | Microsoft Entra Password Protection with global banned password list | Microsoft Entra Password Protection with custom banned password list |
|---|---|---|
| Cloud-only users | Microsoft Entra ID Free | Microsoft Entra ID P1 or P2 |
| Users synchronized from on-premises AD DS | Microsoft Entra ID P1 or P2 | Microsoft Entra ID P1 or P2 |
OS and feature requirements
Proxy
The following requirements apply to the Microsoft Entra Password Protection proxy service:
- Windows Server 2012 R2 or later.
- .NET 4.7.2 installed or higher.
- Do not install on a RODC (Read-Only Domain Controller).
- Allow outbound TLS 1.2 HTTP traffic.
- A Global Administrator account is required to register the Microsoft Entra Password Protection proxy service for the first time in a given tenant.
- Network access to the endpoints: https://login.microsoftonline.com , https://enterpriseregistration.windows.net , and https://autoupdate.msappproxy.net .
The Microsoft Entra Password Protection proxy service does upgrade automatically. The automatic upgrade uses the Microsoft Entra Connect Agent Updater service, which is installed side by side with the proxy service.
DC Agent
The following requirements apply to the Microsoft Entra Password Protection DC agent:
- Windows Server 2012 R2 or later.
- .NET 4.7.2 installed or higher.
- Do not install on a RODC (Read-Only Domain Controller).
- Distributed File System Replication (DFSR) for sysvol replication. If your domain isn’t already using DFSR, you must migrate from RFS (File Replication System – the predecessor to DFSR) to DFSR before installing Microsoft Entra Password Protection.
The Microsoft Entra Password Protection DC agent does not upgrade automatically. Instead, a manual upgrade is accomplished by running the latest version of the AzureADPasswordProtectionDCAgentSetup.msi software installer. The latest version of the software is available on the Microsoft Download Center .
How it works
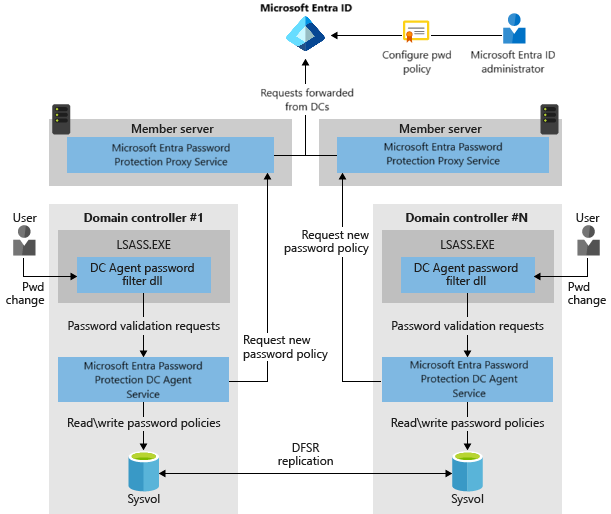
- The Microsoft Entra Password Protection Proxy service runs on any domain-joined machine in the current AD DS forest. The service’s primary purpose is to forward password policy download requests from DCs to Microsoft Entra ID and then return the responses from Microsoft Entra ID to the DC.
- The password filter DLL of the DC Agent receives user password-validation requests from the operating system. The filter forwards them to the DC Agent service that’s running locally on the DC.
- The DC Agent service of Microsoft Entra Password Protection receives password-validation requests from the password filter DLL of the DC Agent. The DC Agent service processes them by using the current (locally available) password policy and returns the result of pass or fail.
Prepare Entra ID
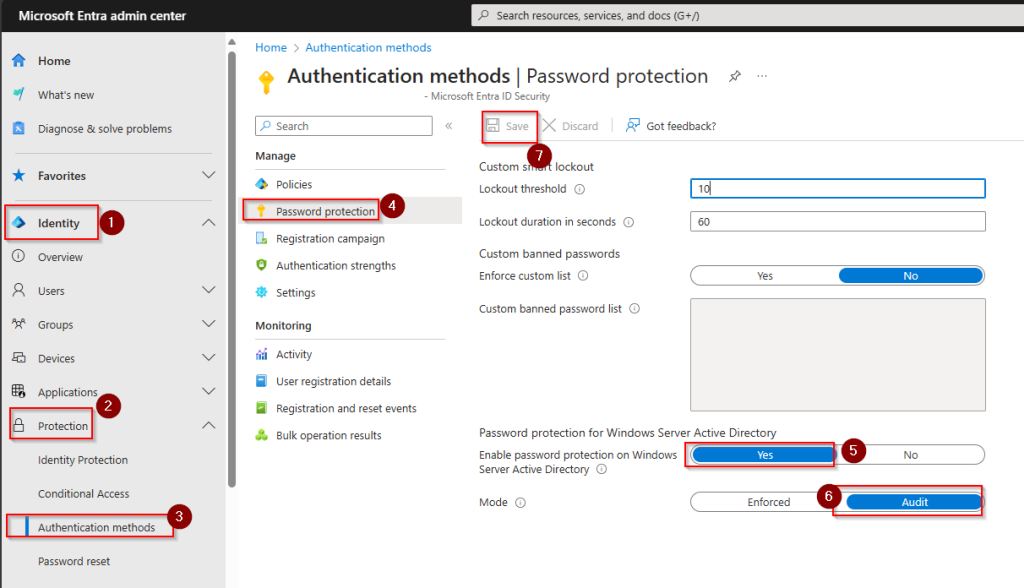
In Entra ID, go to Identity, Protection, Authentication Methods and then Password Protection.
Ensure that “Enable password protection on Windows Server Active Directory” is set to Yes, and mode is set to Audit.
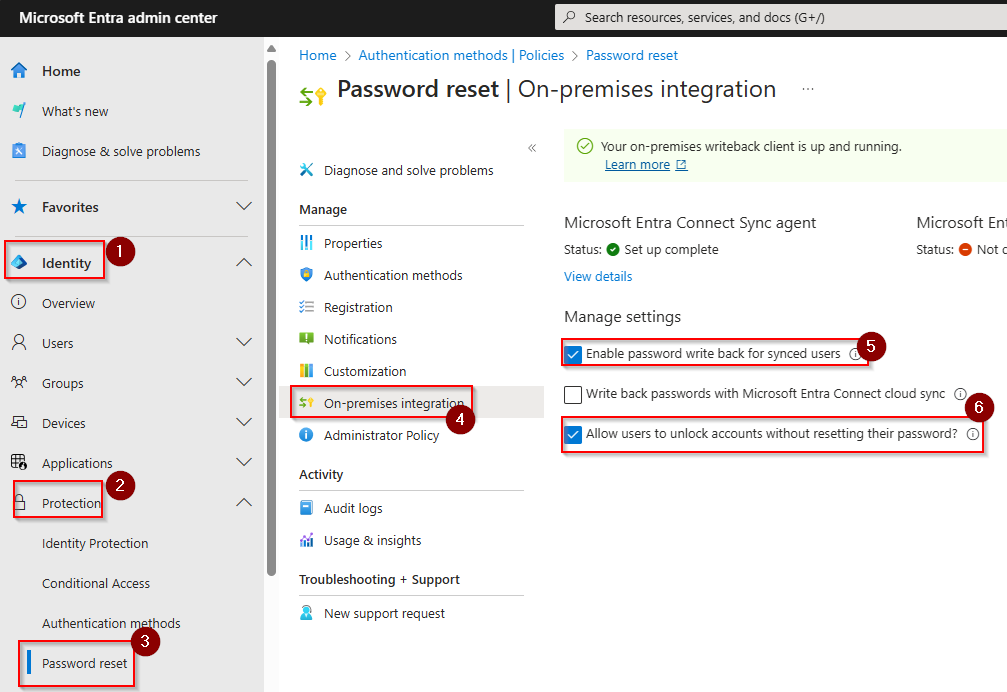
In Entra ID, go to Identity, Protection, Password reset and then On-premises integration.
Ensure that “Enable password writeback for synced users” and “Allow users to unlock accounts without resetting their passwords” and enabled. Then save the changes.
Prepare Entra Connect Sync
On the Windows server there Entra Connect Sync is installed, Open Entra ID Connect as administrator. Press Contiune.
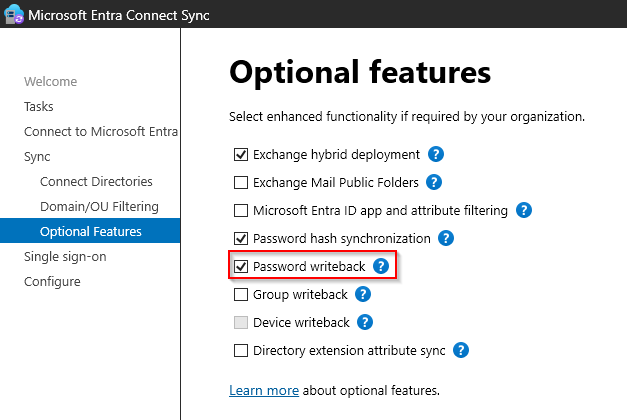
Select “Customize synchronization options”.
And then under Optional Features, make sure “Password writeback” is enabled:
Download software
Download the required software from Microsoft Download Center:
https://www.microsoft.com/en-us/download/details.aspx?id=57071
Install Microsoft Entra Password Protection proxy service
DO NOT INSTALL PROXY ON A DOMAIN CONTROLLER, ONLY USE MEMBER SERVERS IN THE DOMAIN.
It is recommend at least two Microsoft Entra Password Protection proxy servers per forest for redundancy.
I will use the Entra Connect Sync member server for this case.
Move the proxy msi installer file to C:\Install and run as admin.
Open PowerShell and run the following commands:Import-Module AzureADPasswordProtectionRegister-AzureADPasswordProtectionProxy -AccountUpn 'chris_ga@domain.com'Register-AzureADPasswordProtectionForest -AccountUpn 'chris_ga@domain.com'
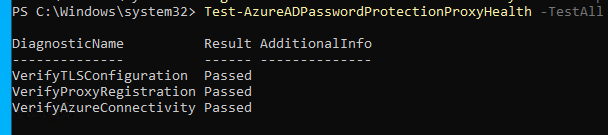
Now test that it works: (should show 3 passed checks)Test-AzureADPasswordProtectionProxyHealth -TestAll
Install Microsoft Entra Password Protection DC Agent Service
Install Microsoft Entra Password Protection DC agent service on the on-premises Domain Controllers.
Install on all domain controllers in the forest.
Move the agent DC install to C:\Install and run as Administrator.
Restart the domain controller. Wait before it is running again before installing on other domain controllers (in setups with only one domain controller, do not restart until a valid maintenance windows is granted by customer)
Verify that the DC agent is healthy by running the following command on each domain controller you have installed the DC agent, via PowerShell opened as Administrator. All tests should pass.
`Test-AzureADPasswordProtectionDCAgentHealth -TestAll`
Troubleshooting
You can use the event log on domain controllers to verify if everything works.
Open Event Log and navigate to Windows Logs, Applications and Services Logs, Microsoft, AzureADPasswordProtection and then DCAgent:
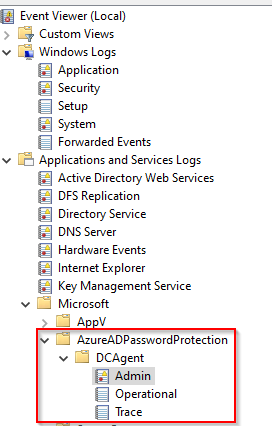
event ID 10025 and event ID 30009: Rejects the password
event ID 10015: Validates the password
Get a summary report showing how many new passwords sets are validated and how many are failed.
`Get-AzureADPasswordProtectionSummaryReport`
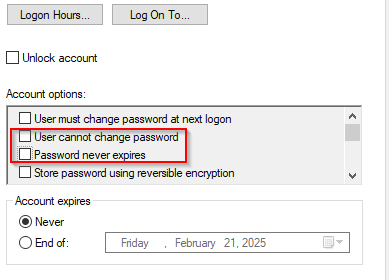
Remember to ensure that users can change their own password and that their password expires in Active Directory Users and Computers (OBS: do not remove the checkmark in “password never expire” without letting the users reset their password first, otherwise users will be locked out and can only regain acces by having an administrator reset their password)
Enforcing Microsoft Entra Password Protection
So far we have configured everyting and monitored if it works.
Now it is truly time to make the switch by enforcing the system.
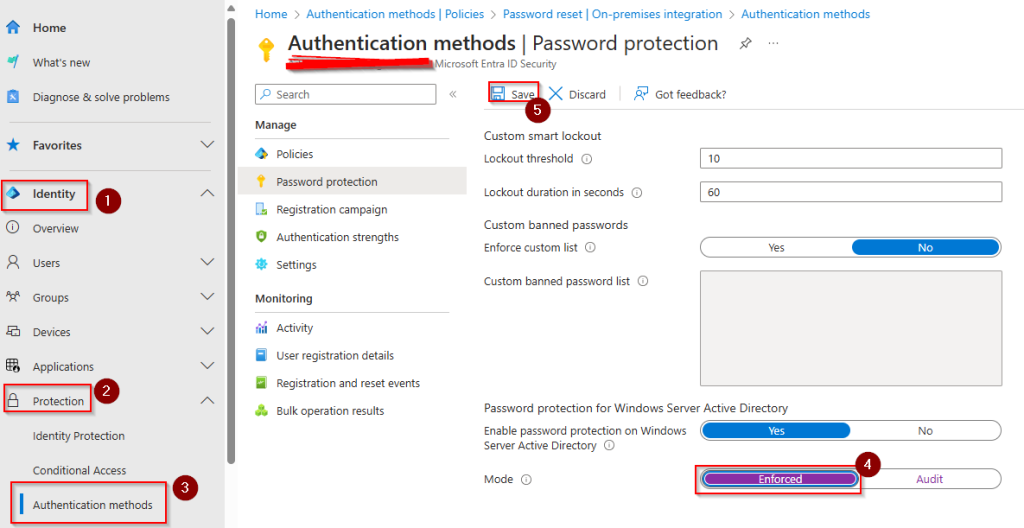
In Entra ID, go to Identity, Protection, Authentication Methods and then Password Protection.
Change Mode to “Enforced” and save the configuration.
Important
To have the changes apply immediately, restart the Azure AD DC agent Sevices on all the Domain Controllers.

Comments